Users access the files that are stored in Assets Server by making use of any of the client applications such as Assets, the Brand portal or Assets for InDesign.
Before they can do this, they need to be given access to these clients and the stored files. This is done by adding the users or user groups to Assets Server and subsequently defining Permissions for these users or user groups. Such Permissions control access to:
- Client applications and their features
- Folders and files in Assets Server
- Metadata fields
- Presets for downloading images
This article describes how to control user access to the client applications and their features.
Capabilities
Controlling access to a client and its features is done by setting up 'Capabilities'. In it, the following aspects are defined:
- The role of the user or user group and the clients that can be accessed.
- Which features within a client the user or user group can use.
Managing Capabilities
Capabilities are assigned to users and user groups as part of assigning Permissions. This is done in the Management Console.
Step 1. Access the Management Console by doing one of the following:
- Access the following URL and log in using system administrator credentials (a 'Super user' account):
<Assets Server URL>/console
- In Assets, access the Avatar menu and choose Management Console.
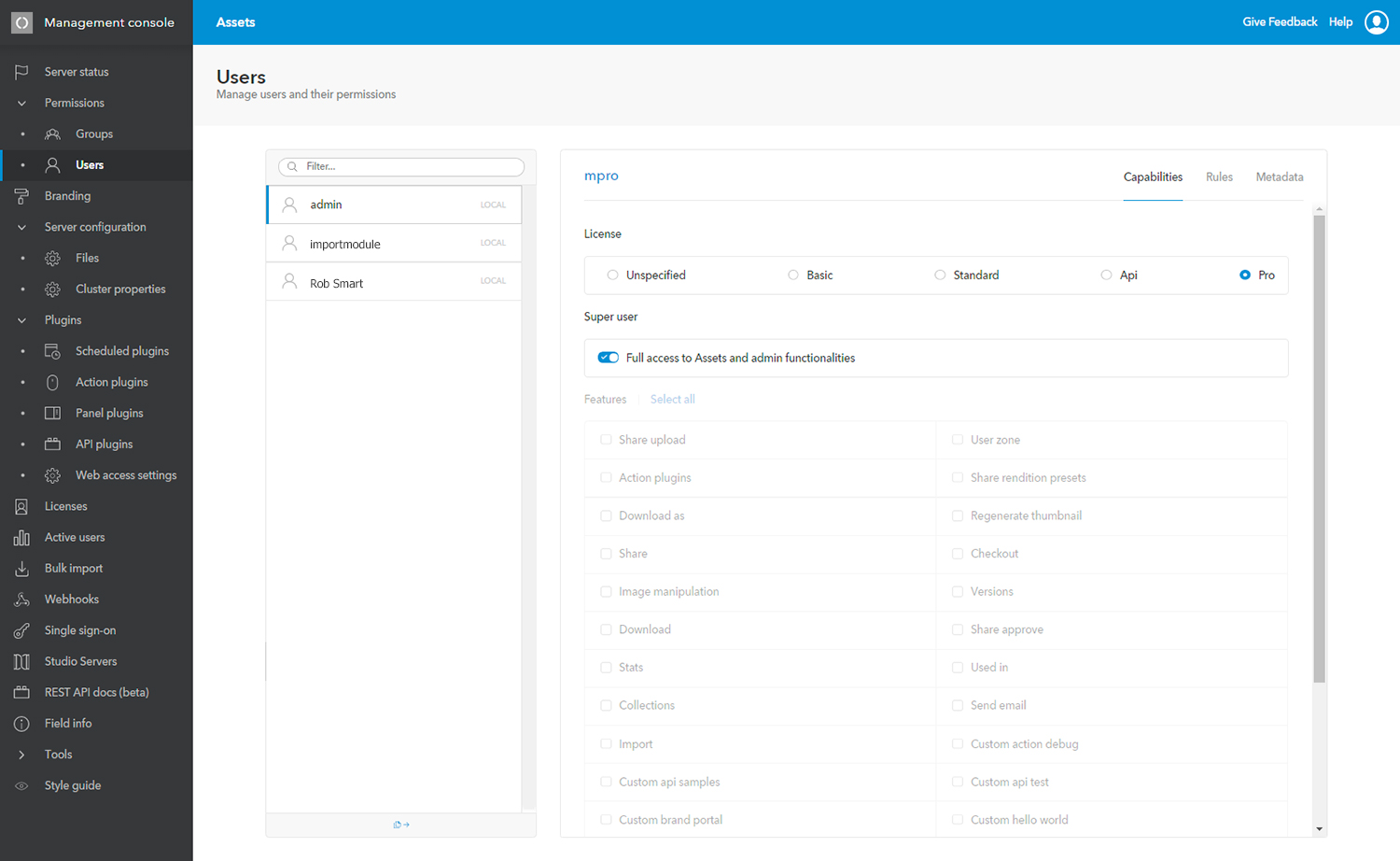
Figure: The Users page in the Management Console.
Step 2. In the menu on the left of the page, choose Permissions followed by User Groups or Users.
Step 3. Use the search options to search for users and/or user groups.
|
Troubleshooting: "LDAP search failed" error appears In certain scenarios, the following error can appear: LDAP search failed: The number of search results exceeds the Active Directory limit. Modify your search to limit the number of results. For more information, see "LDAP search failed" error when searching for users in Assets Server. |
Step 4. Select the user or user group to which you want to assign a Capability.
Step 5. Set up Capabilities (see below).
1. Setting the user role and client access
The first step is to define the role of the user and the clients that can be accessed.
Both are done by assigning a specific user license.
|
Notes:
|
|
Role: Unspecified user Required license: Unspecified; the license is inherited from the user group that the user is added to. In a typical workflow, a user will have the Unspecified role assigned and will be added to one or more groups. With the Unspecified role, a user will inherit the user license that is set for the group that they are added to. Note: When a user is a member of multiple groups with different user license settings, the most feature-rich license will be used. When no user license type is set for a user or one of its groups, the least feature-rich license will be used (a Basic license if available, else a Standard license, or else a Pro license). |
|||
|
Role: Basic user Required license: Basic. Use this role for asset consumers who only need to search, download, and share assets. |
|||
|
Role: Standard user Required license: Standard. Use this role for asset contributors who mainly need to import and edit assets. |
|||
|
Role: API Required license: API. Use this role when connecting to Assets Server through an API. In Assets 6.49 or higher, an API license can be combined with a super user role. This makes it possible to automate tasks for which a regular API user does not have sufficient permissions. |
|||
|
Role: Pro Required license: Pro. Use this role for users who perform multiple roles. Optionally combine it with a super user role. |
|||
|
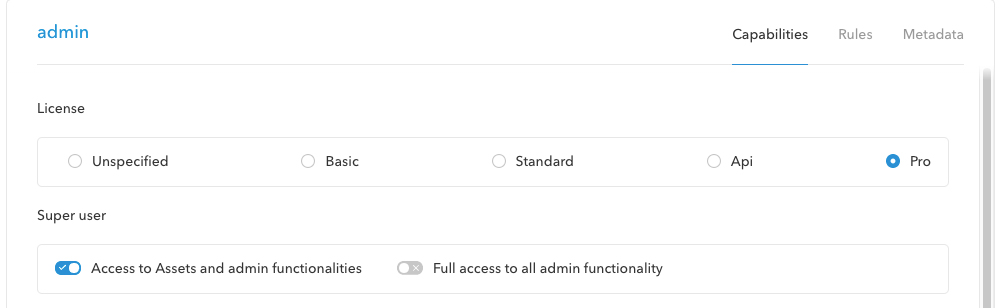
Role: Super user: Access to Assets and admin functionalities This role allows users full access to Assets, but limited access to the Management Console of Assets Server. Use this role in environments where there is a split of responsibility between managing the environment and the functional setup. Requires Assets Server 6.61 or higher. Required license: Pro or API. In combination with a Pro license:
1 Only the configuration options that are defined in the following option can be seen and edited by this user:
Note: We recommend to only give access to options that do not require a server restart or break the system in some other way.
Features in the Management Console that these users do not have access to are:
In combination with an API license: An API admin user can perform the same tasks as a Pro admin user with the exception of the following:
|
|||
|
Role: Super user: Full access to all admin functionality Required license: Pro or API. Description:
|
2. Setting access to the client features
The next step is to define the client features that the user can use. Be aware that features may be grayed-out when:
- The user has the role of 'Super user'. Such users have full access to the system.
- The chosen license does not allow access to the feature.
Features can be assigned manually or as part of copying Permissions from another user or group.
Assigning a feature manually
Step 1. Access the Users page or User groups page (see above).
Step 2. From the list of user groups, select the user group to which a feature needs to be assigned.
Tip: Use the Filter to narrow down the results in the list by typing any part of a name.
Step 3. From the list of features (see below), select the features that need to be assigned to the group.
Copying Permissions
Copying Permissions is an efficient way of quickly assigning an existing set of Permissions to a user or group.
Warning: When copying, all existing Permissions for that user or user group will be replaced.
Step 1. From the list of users or user groups, choose the user or group from which you want to copy the assigned Permissions.
Step 2. At the bottom of the list, click the Copy button.
The 'Copy Permissions To' window appears.
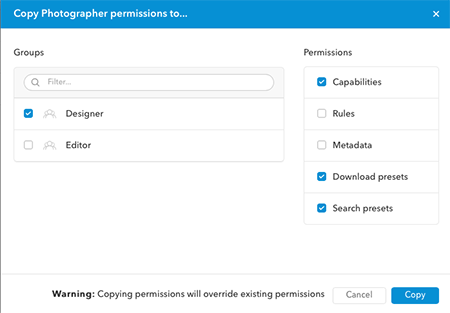
Step 3. From the list of users or groups, choose the user or group to which you want to copy the Permissions.
Step 4. In the list of Permissions, select which type of Permissions should be copied.
Step 5. Click Copy.
The Permissions are copied.
List of features
The following table shows the list of default Capabilities in Assets Server. Shown are the name as it appears in the Management Console as well as the internal name used for configuring the requiredRole setting of a plug-in (where applicable).
Note: The list in the Management Console can also contain custom Capabilities as defined in Action plug-ins or Panel plug-ins. If such a plug-in is made active therefore, you might see more Capabilities listed in the Management Console than shown in the table.
| Feature | Available in | Details | |
|---|---|---|---|
|
Share upload (Formerly known as 'Create upload requests') |
Assets |
Allows users to create a Share Link to which a user can upload files. Also requires the Share feature to be enabled (see below). |
|
| Action plug-ins | Assets |
Allows users to use plug-ins in Assets. |
|
| Download as ROLE_DOWNLOAD_AS |
Allows users to choose the format in which to download the preview of an asset in (JPG, PNG or TIFF format) and specify settings for the size, resolution and metadata of that downloaded preview. A preview can only be downloaded for images for which the View Preview rule is set. |
||
| Share ROLE_SHARE |
Allows users to create a Share Link, used for sharing assets with others. |
||
| Image manipulation ROLE_IMAGE_MANIPULATION |
Assets |
Allows users to rotate or flip images in Assets without having to open the image in an external editor. Requires 'View' and 'Edit metadata' Permission types to be assigned. |
|
| Download ROLE_DOWNLOAD |
Allows users to download assets in the following ways:
An asset can only be downloaded when the Use original permission is set for the user. Previews can only be downloaded when the View Preview permission for the user. |
||
| Used in ROLE_USED_IN |
Assets | Makes the 'Used in Studio' panel available which allows users to see where in the Studio workflow a file is used. | |
| Collections ROLE_COLLECTIONS |
Assets | Allows a user to create and manage Collections. | |
| Import ROLE_IMPORT |
Management Console |
Allows the user to import assets, for example by using the Bulk Import feature. The user can only import assets into folders for which they have "CREATE" permissions. Files can only be imported into folders for which the user has Create permission. |
|
| User zone ROLE_USER_ZONE |
Grants the user access to a private user folder to which they have full access. This folder is located in the /Users folder and the user account name is used as the folder name. All users that have access to Assets will automatically have a private folder available.
|
||
|
Share Rendition presets (Formerly known as 'Share Download presets') |
When enabled, any Download Presets are shared with all users within the group(s) that the user is a member of. Also required when using the 'Share upload' feature (see above). |
||
| Regenerate thumbnail ROLE_REGENERATE_THUMBNAIL |
Assets |
Makes the 'Regenerate thumbnail' command available in the context menu of an asset. Allows the user to regenerate the thumbnail and preview of an asset. |
|
| Checkout ROLE_CHECKOUT |
Assets |
Allows users to open files for editing by checking-out the file, editing it in some way and checking-in the file again. The user can only check out assets for which they have Edit permission. |
|
| Versions ROLE_VERSIONS |
Assets |
Allows users to view and restore versions of an asset. To promote or revert a version, Edit permission is required. To delete a version, Delete permission is required. This feature is not needed to create a version. Version creation happens automatically when a file is checked in. |
|
| Share approve ROLE_SHARE_APPROVE |
Allows the user to create a Share link, used for letting another user approve or reject assets. Also requires the Share feature to be enabled. |
||
| Taxonomy ROLE_TAXONOMY |
- | Deprecated, not used. | |
| Send email ROLE_SEND_EMAIL |
API | Allows the user to send e-mails by using the E-mail API. | |
|
Delete |
Assets |
Requires Assets Server 6.85 or higher. Controls the availability of the Delete command in the context menu of a file.1 Tip: Use this in combination with the Trash Can plug-in; when disabled, users will have access to the Move to Trash Can option while the Delete command is hidden from the context menu. |
1 The Delete Capability is closely related to the Delete permission in a Rule which controls if users are actually permitted to permanently delete files.
Observe the following differences in behavior when setting both options:
| Scenario | Delete Capability | Delete Permission | Behavior |
|---|---|---|---|
| 1 | Enabled | Enabled | The Delete command is available and enabled in the context menu; files can be permanently deleted. |
| 2 | Enabled | Disabled | The Delete command is available in the context menu but grayed out; users can see the command but cannot use it. |
| 3 | Disabled | Enabled | The Delete command is hidden from the context menu; users are unable to see and use it. Files still have the delete permission assigned, which can be useful for the requiredPermissionMask setting (the D permission) of Action plug-ins. |
| 4 | Disabled | Disabled | The Delete command is hidden from the context menu and the delete permission is removed for all files; files cannot be deleted by users or Action plug-ins. |
Comments
0 comments
Please sign in to leave a comment.