By integrating LDAP (Lightweight Directory Access Protocol) in Enterprise Server, user authorizations can be better controlled and user accounts can be better maintained.
With LDAP enabled — which is optional — user authorization is controlled through the LDAP Server rather than through Enterprise Server.
The process is shown in the following overview:
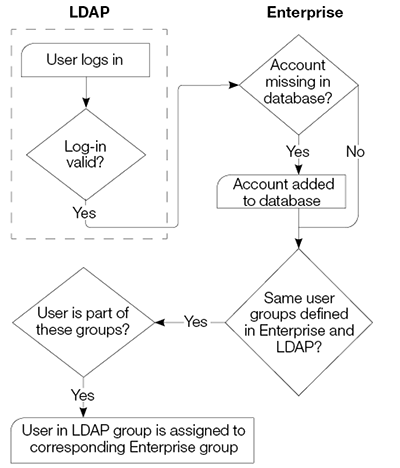
- When a user logs in, it is validated by LDAP.
- If the account is validated, Enterprise synchronizes it by also making it available in its own database (when missing).
- It will then check if there are any user groups that are defined both in Enterprise and LDAP.
- Only taking those groups into account, if a user is assigned to a certain group in LDAP, that user will be assigned to the corresponding Enterprise user group and removed from other groups as well.
|
Notes:
|
Info: This article contains references to macOS. Running Enterprise Server 10 on macOS is only supported on Enterprise Server version 10.8 or lower.
Enabling LDAP in Enterprise Server
Step 1. In the configserver.php file for Enterprise Server, locate the List of LDAP servers section.
Tip: (For Enterprise Server 10.1 or higher only) Easily manage and configure settings of all configuration files by adding them to a single configuration file.
<Enterprise Server path>/Enterprise/config
/*
// -----------------------------------------------------------------------------
// List of LDAP servers. See '/server/dataclasses/LDAPServer.class.php' for more info.
// -----------------------------------------------------------------------------
require_once BASEDIR.'/server/dataclasses/LDAPServer.class.php';
// Options for the LDAP server.
// To manage groups in Enterprise and not LDAP set GROUPMEMBER_ATTRIB to null.
// For Windows Active Directory usually:
// 'AUTH_USER' => '%username%@myldap.mycompany.local',
// 'AUTH_PASSWORD' => '%password%',
// 'USERNAME_ATTRIB' => 'sAMAccountName',
// 'GROUPMEMBER_ATTRIB' => 'memberof',
// 'ATTRIB_MAP' => array('FullName' => array( 'name' ), 'EmailAddress' => 'mail'),
// 'FULLNAME_SEPARATOR' => ', ',
// 'GROUP_CLASS' => 'group',
// 'EXCLUDE_USERNAMES' => array('woodwing'),
// 'EMAIL_NOTIFICATIONS' => true
// For OpenLDAP usually:
// 'AUTH_USER' => null,
// 'AUTH_PASSWORD' => null,
// 'USERNAME_ATTRIB' => 'uid',
// 'GROUPMEMBER_ATTRIB' => 'memberof',
// 'ATTRIB_MAP' => array('FullName' => array( 'name' ), 'EmailAddress' => 'mail'),
// 'FULLNAME_SEPARATOR' => ', ',
// 'GROUP_CLASS' => 'posixGroup',
// 'EXCLUDE_USERNAMES' => array('woodwing'),
// 'EMAIL_NOTIFICATIONS' => true
//
$ldap_options = array(
'AUTH_USER' => '%username%@myldap.mycompany.local',
'AUTH_PASSWORD' => '%password%',
'BASE_DN' => 'DC=myldap,DC=mycompany,DC=local',
'USERNAME_ATTRIB' => 'sAMAccountName',
'GROUPMEMBER_ATTRIB' => 'memberof',
'ATTRIB_MAP' => array(
'FullName' => array( 'name' ),
'EmailAddress' => 'mail'),
'FULLNAME_SEPARATOR' => ', ',
'GROUP_CLASS' => 'group',
'EXCLUDE_USERNAMES' => array('woodwing'),
'EMAIL_NOTIFICATIONS' => true
);
define( 'LDAP_SERVERS', serialize( array(
// LDAPServer( LDAP server IP, port number, Primary DNS Suffix, Options: see above )
new LDAPServer( 'myldap_server', null, 'myldap.mycompany.local', $ldap_options )
)));
*/Step 2. Move the following outside of the comments so that they become active:
- The first line require_once BASEDIR.'/server/dataclasses/LDAPServer.class.php';
- The last sections $ldap_options and define 'LDAP_SERVERS'
/*
// ------------------------------------------------------------------------------
// List of LDAP servers. See '/server/dataclasses/LDAPServer.class.php' for more info.
// ------------------------------------------------------------------------------
// Options for the LDAP server.
// To manage groups in Enterprise and not LDAP set GROUPMEMBER_ATTRIB to null.
// For Windows Active Directory usually:
// 'AUTH_USER' => '%username%@myldap.mycompany.local',
// 'AUTH_PASSWORD' => '%password%',
// 'USERNAME_ATTRIB' => 'sAMAccountName',
// 'GROUPMEMBER_ATTRIB' => 'memberof',
// 'ATTRIB_MAP' => array('FullName' => array( 'name' ), 'EmailAddress' => 'mail'),
// 'FULLNAME_SEPARATOR' => ', ',
// 'GROUP_CLASS' => 'group',
// 'EXCLUDE_USERNAMES' => array('woodwing'),
// 'EMAIL_NOTIFICATIONS' => true
// For OpenLDAP usually:
// 'AUTH_USER' => null,
// 'AUTH_PASSWORD' => null,
// 'USERNAME_ATTRIB' => 'uid',
// 'GROUPMEMBER_ATTRIB' => 'memberof',
// 'ATTRIB_MAP' => array('FullName' => array( 'name' ), 'EmailAddress' => 'mail'),
// 'FULLNAME_SEPARATOR' => ', ',
// 'GROUP_CLASS' => 'posixGroup',
// 'EXCLUDE_USERNAMES' => array('woodwing'),
// 'EMAIL_NOTIFICATIONS' => true
//
*/
require_once BASEDIR.'/server/dataclasses/LDAPServer.class.php';
$ldap_options = array(
'AUTH_USER' => '%username%@myldap.mycompany.local',
'AUTH_PASSWORD' => '%password%',
'BASE_DN' => 'DC=myldap,DC=mycompany,DC=local',
'USERNAME_ATTRIB' => 'sAMAccountName',
'GROUPMEMBER_ATTRIB' => 'memberof',
'ATTRIB_MAP' => array(
'FullName' => array( 'name' ),
'EmailAddress' => 'mail'),
'FULLNAME_SEPARATOR' => ', ',
'GROUP_CLASS' => 'group',
'EXCLUDE_USERNAMES' => array('woodwing'),
'EMAIL_NOTIFICATIONS' => true
);
define( 'LDAP_SERVERS', serialize( array(
// LDAPServer( LDAP server IP, port number, Primary DNS Suffix, Options: see above )
new LDAPServer( 'myldap_server', null, 'myldap.mycompany.local', $ldap_options )
)));Step 3. Fill out the ldap_options as required. For an explanation of each option, see the comments in the configserver.php file. See also Mapping LDAP users with Enterprise Server user accounts below.
Step 4. Enter your LDAP server configuration in the LDAP_SERVERS object. For details, see the comments in the configserver.php file.
Mapping LDAP users with Enterprise Server user accounts
Mapping LDAP with the properties for a user in Enterprise Server is done through the 'ATTRIB_MAP' setting of the $ldap_options in the configserver.php file.
Tip: (For Enterprise Server 10.1 or higher only) Easily manage and configure settings of all configuration files by adding them to a single configuration file.
The following Enterprise properties can be mapped:
- FullName. Possible values:
- 'name' For mapping to the full name as set in LDAP
- 'sn' For mapping to the surname as set in LDAP
- 'cn' For mapping to the common name as set in LDAP
- array('givenName', 'sn') Use an array to map to multiple LDAP properties
Note: The separator used in the array is the one defined in FULLNAME_SEPARATOR. Its default value is a comma followed by a space ', '.
|
Examples:
|
- EmailAddress
- Language
- TrackChangesColor
- Organization
- Location
|
Note: (For Enterprise Server 10.7 and higher) When LDAP is used, the values of the following fields are managed by LDAP and are therefore disabled on the User Maintenance page:
|
Enabling LDAP in PHP
To use LDAP authorization your PHP installation must be LDAP enabled. This means that the following PHP extensions must be installed:
- On Windows:
- php_ldap.dll
- ssleay32.dll
- libeay32.dll
- On Mac/Linux:
- php_ldap.so
- openssl.so
Testing the installation
To verify the installation, run the LDAP test on the Enterprise Health Check page.
Step 1. In Enterprise Server, click Advanced in the Maintenance menu or on the Home page.
A page with all advanced Maintenance features appears.
Step 2. Click Health Check.
The Health Check page appears.
Step 3. Click Clear All to clear all selected tests.
Step 4. Select one of the following tests:
- For Enterprise Server 10.7.x or higher: Authentication
- For Enterprise Server 10.x – 10.6.x: LDAP
Step 5. Click Test.
The test result should appear as 'OK'. In case the test fails, follow the instructions on the page.
Synchronizing user accounts and user groups
User groups that have already been set up in LDAP can be synchronized by importing them into Enterprise Server. User accounts are synchronized after successfully logging in, after which an account is created and the user's (LDAP) group memberships are synchronized with Enterprise.
The following data is synchronized:
- User Data: ID, Full Name, Password, and E-mail.
- Group Data: Name, Description.
- Memberships: User groups that are defined both in Enterprise and LDAP are assigned to the user logging in.
Note: When changing the user name in LDAP, Enterprise will automatically update the short user name in its system.
Importing user groups
Step 1. Access the Overview of User Groups page.
In the Maintenance menu or on the Home page, click User Groups.
Step 2. Below the list of groups, click Import User Group.
A page showing all created LDAP user groups appears.
Step 3. Select the user groups to import.
Step 4. Click Import Selection.
Note: This option is only available if Open LDAP or Active Directory are installed.
Step 5. Select the network domain from where you want to import from.
Step 6. (Optional) Apply a query such as “*Admin*” to narrow down the results.
Step 7. Tag the groups you want to import.
Step 8. Click Import.
Step 9. Add the imported groups to the User Authorizations section of the Brand that the users should have access to.
Step 9a. On the Brand Maintenance page, click Add in the User Authorizations section.

Figure: The User Authorizations section on a Brand Maintenance page.
The Authorization Maintenance page appears.
Step 9b. From the User Groups list, choose the user group that needs to be added.
Step 9c. Click Add Authorization.
Lists appear for the Category, Workflow Status and Access Profile.
Step 9d. Make a choice from each list.
Note: Use '<All>' to assign an Access Profile to all Categories and/or Workflow Statuses or choose a Category or Workflow Status from the list to assign the Access Profiles to that combination only.
Example: Imagine an Access Profile named 'Delete disabled' in which the options for deleting files have been disabled. When assigning user group A to Category '<All>', Status '<All>' and Profile 'Delete disabled', all members of user group A will not be able to delete any of the files in the Brand. When assigning user group B to Category '<All>', Status 'For publication' and Profile 'Delete disabled', users from group B cannot delete any files from the Brand that are set to the Workflow status 'For publication'. They can however delete all other files.
Step 9e. Click Update.
Step 9f. (Optional, only necessary when not having chosen '<All>' for both the Category and Workflow Status lists) Continue adding Authorizations for as many Category/Workflow Status combinations as necessary.
Note: When no authorizations are assigned, users can log in but cannot access any of the Brands they have been added to.
Verifying if users are assigned to user groups
Check the column named 'Assigned to User Groups' on the Overview of Users page.
A value of 'Yes' or 'No' can be shown:
- 'Yes' means: the user has been assigned to one or more user groups and therefore has access to one or more Brands.
- 'No' means: the user is created by a content source (such as WoodWing Elvis) but has not yet been assigned to a user group and therefore does not have access to any Brands.
Note: The reason why the user has not been assigned to a user group could be because the user has never logged in and its settings have therefore not been automatically updated yet.
Analysis:
This happens when the LDAP option 'GROUPMEMBER_ATTRIB’ in the configserver.php file (used for automatically adding a user to a user group) is set to ‘null’. This means that the user is not automatically added to a user group. However, the Overview of Users page incorrectly indicates that the user has been assigned.
Solution:
Add the user manually to one or more user groups.
Notes
- When LDAP has been configured, users need to enter the short user name when logging in.
Comments
1 comment
For information about configuring two or more LDAP Servers, see the Feedback Forum.
Please sign in to leave a comment.